Last year I was browsing Hacker News (ycombinator.com) and I came across this post. It’s about an open source Rust project called Bore.
Bore is a modern, simple TCP tunnel in Rust that exposes local ports to a remote server, bypassing standard NAT connection firewalls. That’s all it does: no more, and no less.
bore/README.md at main · ekzhang/bore (github.com)
If you are not aware of what a TCP tunnel like Bore is, the basic gist of it is you can expose a service running on your local system to the internet relatively easy by creating a “tunnel” between your machine and (in this case) a Bore server. Here is how that would look for those visual learners:
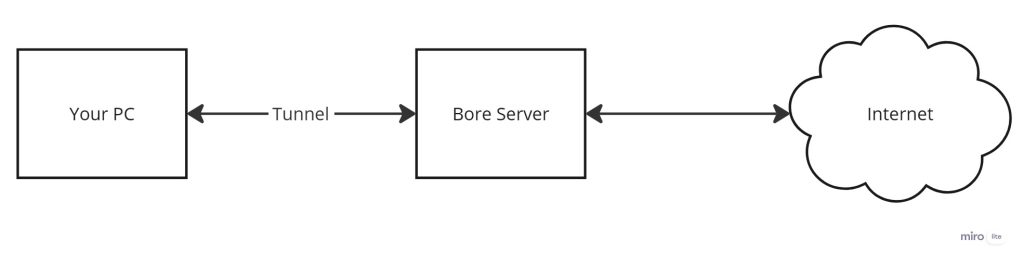
Bore is actually really simple to use, just install it and run:
bore local <local_port> --to <bore_server>
And that’s it. After that you’re service is exposed and accessible via the internet. Now, conveniently Bore is already running a server that you can tunnel your local services too: bore.pub. With that, you don’t even need to run your own Bore server, just connect your local service to bore.pub and connect away.
But with bore.pub being public, anyone can just run a port scan to see all the services running on the bore.pub server. So I did just that.
[user@server ~]# nmap -p 1024-65535 bore.pub
Starting Nmap 7.91 ( https://nmap.org ) at 2023-05-24 00:28 UTC
NmNmap scan report for bore.pub (159.223.171.199)
Host is up (0.00045s latency).
Not shown: 64441 closed ports
PORT STATE SERVICE
1338/tcp open wmc-log-svc
1342/tcp open esbroker
2515/tcp open facsys-router
3000/tcp open ppp
3799/tcp open radius-dynauth
5353/tcp open mdns
5354/tcp open mdnsresponder
6067/tcp open unknown
6603/tcp open unknown
7117/tcp open rothaga
7129/tcp open scenccs
7177/tcp open unknown
7351/tcp open swx
7835/tcp open unknown
8000/tcp open http-alt
8080/tcp open http-proxy
9469/tcp open unknown
9999/tcp open abyss
10466/tcp open unknown
11205/tcp open unknown
11784/tcp open unknown
12127/tcp open unknown
12150/tcp open unknown
12396/tcp open unknown
12397/tcp open unknown
12699/tcp open unknown
13473/tcp open unknown
13953/tcp open unknown
16580/tcp open unknown
17199/tcp open unknown
17400/tcp open unknown
18010/tcp open unknown
18892/tcp open unknown
19415/tcp open unknown
19519/tcp open unknown
20206/tcp open unknown
21489/tcp open unknown
24237/tcp open unknown
27489/tcp open unknown
29255/tcp open unknown
31063/tcp open unknown
31202/tcp open unknown
32751/tcp open unknown
33120/tcp open unknown
34281/tcp open unknown
35008/tcp open unknown
37318/tcp open unknown
37899/tcp open unknown
38804/tcp open unknown
39195/tcp open unknown
41040/tcp open unknown
41558/tcp open unknown
43500/tcp open unknown
44016/tcp open unknown
44423/tcp open unknown
44424/tcp open unknown
44788/tcp open unknown
47474/tcp open unknown
47989/tcp open unknown
49909/tcp open unknown
53668/tcp open unknown
55833/tcp open unknown
59182/tcp open unknown
60050/tcp open unknown
60207/tcp open unknown
60283/tcp open unknown
60561/tcp open unknown
62962/tcp open unknown
63177/tcp open unknown
64067/tcp open unknown
64531/tcp open unknownI just did a quick port scan to see what ports are open running a service. And I actually discovered something pretty interesting, most of the open ports between 10466 – 64531 are running a leaked version of NovelAI. I went around digging for a couple minutes and found the following Reddit post (possibly NSFW?). That post links to a Google Collab page that gives instructions on how to run your own instance of NovelAI and expose it using bore.pub. I have to assume that this is why there are so many instances running? I don’t know. I haven’t really gotten around to checking out the ports 1338 – 9999 but plan to shortly after this blog post.
I’ve had this fascination with just checking out what people are running with Bore since discovering it. I’ve seen people running phishing websites and have seen others discover C2 nodes being run with on it. It has me wondering about the personal liability of the individual running the bore.pub server. Are they responsible is CSAM is accessible through their server? Or if a hacking group uses it as their C2 node? Probably something I need to learn more about.
That’s all for now. Thanks!
Leave a Reply